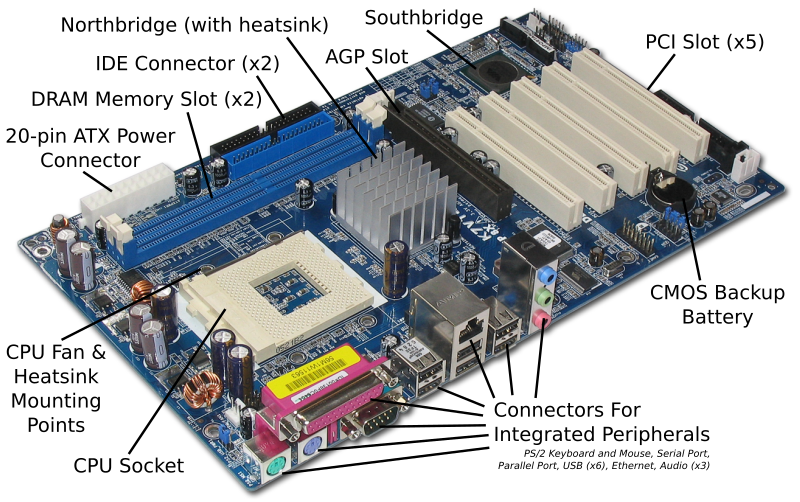
Computers should have alarm systems to guard them from any attacks such as viruses and data corruption. The alarm system is the security measures that we take to ensure its safety.
DATA PROTECTION
We need to protect the data in the computer as it may somehow get lost or corrupted due to some viruses or mishap like fire, flood, lightning, machine failures and even human errors.
There are a few ways to protect the information namely:
• make backup files
• detect the virus and clean the computer
• warn others on virus attacks
1) BACKUP FILES
Users can do backups of file systems by:
keeping the duplicated files in external storage such as in the floppy disk and thumb drive
do backup frequently
2) DETECT VIRUS AND DO CLEANUP
A computer virus is able to affect and infect the way the computer works. Viruses can be detected when we run an antivirus. We can also delete the infected files and documents.
3) WARN OTHERS ON VIRUS ATTACK
We can warn others on virus attacks or new viruses by sending e-mails to them.
DETECTING ILLEGAL ACCESS TO SYSTEMS
The computer system is able to detect any illegal access to the system by a user who does not have any authorisation. Basically, a corporation will simply use tcpwrappers and tripwire to detect any illegal access to their system. User's access will be reviewed periodically by computer operations. On going internal audits will be made to ensure detection of violations of security and unauthorised modifications to software and data .
TCPWRAPPERS
Tcpwrappers stop the attempted connection
examines its configuration files
will decide whether to accept or reject the request.
Tcpwrappers will control access at the application level, rather than at the socket level like iptables and ipchains. The system will run tcpwrappers to log access to ftp, tftp, rch, rlogin, rexec and telnet.
TRIPWIRE
Tripwire will detect and report on any changes in the thousands of strategic system files.
The system will run tripwire to determine if system files have changed.
PREVENTING ILLEGAL ACCESS TO SYSTEMS
Ways to prevent illegal access to systems:
1. Run anlpassword to make password cracking difficult.
2. Run tcpwrappers to check if the name for an ip address can be provided by DNC
3. Use a callback system to prevent unauthorised use of stolen passwords.
PREVENTING ILLEGAL ROOT ACCESS
Sudo stands for (Superuser do) and is a program in Unix, Linux and similar operating systems such as Mac OS X that allows users to run programs in the form of another user (normally in the form of the system's superuser).
Sudo allows a permitted user to execute a command as the superuser or another user, as specified in the sudoers file.
PATCH
Patch supplies small updates to software, provided that the source code is available.
Patch is a name of an UNIX utility. It applies a script generated by the different program to a set of files that allows changes from one file to be directly applied to another file.
Resources are not enough to patch all security holes that we hear about through the bugtraq list.
DATA PROTECTION
We need to protect the data in the computer as it may somehow get lost or corrupted due to some viruses or mishap like fire, flood, lightning, machine failures and even human errors.
There are a few ways to protect the information namely:
• make backup files
• detect the virus and clean the computer
• warn others on virus attacks
1) BACKUP FILES
Users can do backups of file systems by:
keeping the duplicated files in external storage such as in the floppy disk and thumb drive
do backup frequently
2) DETECT VIRUS AND DO CLEANUP
A computer virus is able to affect and infect the way the computer works. Viruses can be detected when we run an antivirus. We can also delete the infected files and documents.
3) WARN OTHERS ON VIRUS ATTACK
We can warn others on virus attacks or new viruses by sending e-mails to them.
DETECTING ILLEGAL ACCESS TO SYSTEMS
The computer system is able to detect any illegal access to the system by a user who does not have any authorisation. Basically, a corporation will simply use tcpwrappers and tripwire to detect any illegal access to their system. User's access will be reviewed periodically by computer operations. On going internal audits will be made to ensure detection of violations of security and unauthorised modifications to software and data .
TCPWRAPPERS
Tcpwrappers stop the attempted connection
examines its configuration files
will decide whether to accept or reject the request.
Tcpwrappers will control access at the application level, rather than at the socket level like iptables and ipchains. The system will run tcpwrappers to log access to ftp, tftp, rch, rlogin, rexec and telnet.
TRIPWIRE
Tripwire will detect and report on any changes in the thousands of strategic system files.
The system will run tripwire to determine if system files have changed.
PREVENTING ILLEGAL ACCESS TO SYSTEMS
Ways to prevent illegal access to systems:
1. Run anlpassword to make password cracking difficult.
2. Run tcpwrappers to check if the name for an ip address can be provided by DNC
3. Use a callback system to prevent unauthorised use of stolen passwords.
PREVENTING ILLEGAL ROOT ACCESS
Sudo stands for (Superuser do) and is a program in Unix, Linux and similar operating systems such as Mac OS X that allows users to run programs in the form of another user (normally in the form of the system's superuser).
Sudo allows a permitted user to execute a command as the superuser or another user, as specified in the sudoers file.
PATCH
Patch supplies small updates to software, provided that the source code is available.
Patch is a name of an UNIX utility. It applies a script generated by the different program to a set of files that allows changes from one file to be directly applied to another file.
Resources are not enough to patch all security holes that we hear about through the bugtraq list.
L19: RELATIONSHIP BETWEEN SECURITY THREATS AND SECURITY MEASURES
SECURITY THREADS
Security threats may come from in many forms. For example, when someone is invading your account information from a trusted bank, this act is considered as a security threat.
Security measures can be used to prevent this invader from getting the account information. For example, the bank can use a firewall to prevent
unauthorised access to its database.
MALICIOUS CODE THREATS VS. ANTIVIRUS AND ANTI-SPYWARE
Security threats include virus, Trojan horse, logic bomb, trapdoor and backdoor, and worm.
Antivirus and anti-spyware can be used to protect the computer from the threats by:
limiting connectivity
allowing only authorised media for loading data and software
enforcing mandatory access controls
blocking the virus from the computer program
HACKING VS. FIREWALL
Hacking is an unauthorised access to the computer system done by a hacker. We can use firewall or cryptography to prevent the hacker from accessing our computers.
A firewall permits limited access to unauthorised users or any activities from the network environment. Cryptography is a process of hiding information by changing the actual information into different representation, for example, an APA can be written as 7&*.
NATURAL DISASTER VS. DATA BACKUP
The natural and environmental disasters may include:
• flood
• fire
• earthquakes
• storms
• tornados
The backup system is needed to backup all data and applications in the computer. With the backup system, data can be recovered in case of an emergency.
THEFT VS. HUMAN ASPECTS
Computer theft can be of two kinds:
can be used to steal money, goods, information and computer resources
the actual stealing of computers, especially notebooks and PDAs
Measures that can be taken to prevent theft:
prevent access by using locks, smart-card or password
prevent portability by restricting the hardware from being moved
detect and guard all exits and record any hardware transported
BE SUPSPICIOUS OF ALL RESULTS
There are many instances where non-programmers develop applications which are not built with proper understanding of software engineering practices. Data produced by such applications may not be correct and may risk corrupting data received from other sources that are not compatible with the application.
Security threats may come from in many forms. For example, when someone is invading your account information from a trusted bank, this act is considered as a security threat.
Security measures can be used to prevent this invader from getting the account information. For example, the bank can use a firewall to prevent
unauthorised access to its database.
MALICIOUS CODE THREATS VS. ANTIVIRUS AND ANTI-SPYWARE
Security threats include virus, Trojan horse, logic bomb, trapdoor and backdoor, and worm.
Antivirus and anti-spyware can be used to protect the computer from the threats by:
limiting connectivity
allowing only authorised media for loading data and software
enforcing mandatory access controls
blocking the virus from the computer program
HACKING VS. FIREWALL
Hacking is an unauthorised access to the computer system done by a hacker. We can use firewall or cryptography to prevent the hacker from accessing our computers.
A firewall permits limited access to unauthorised users or any activities from the network environment. Cryptography is a process of hiding information by changing the actual information into different representation, for example, an APA can be written as 7&*.
NATURAL DISASTER VS. DATA BACKUP
The natural and environmental disasters may include:
• flood
• fire
• earthquakes
• storms
• tornados
The backup system is needed to backup all data and applications in the computer. With the backup system, data can be recovered in case of an emergency.
THEFT VS. HUMAN ASPECTS
Computer theft can be of two kinds:
can be used to steal money, goods, information and computer resources
the actual stealing of computers, especially notebooks and PDAs
Measures that can be taken to prevent theft:
prevent access by using locks, smart-card or password
prevent portability by restricting the hardware from being moved
detect and guard all exits and record any hardware transported
BE SUPSPICIOUS OF ALL RESULTS
There are many instances where non-programmers develop applications which are not built with proper understanding of software engineering practices. Data produced by such applications may not be correct and may risk corrupting data received from other sources that are not compatible with the application.
L18: SECURITY MEASURES
Security measures mean the precautionary measures taken toward possible danger or damage. There are 6 type of security measures.
1) DATA BACKUP
Data Backup is a program of file duplication. Backups of data applications are necessary so that they can be recovered in case of an emergency.
2) CRYPTOGRAPHY
Cryptography is a process of hiding information by altering the actual information into different representation, for example, an APA can be written as I? X.
Almost all cryptosystems depend on a key such as a password like the numbers or a phrase that can be used to encrypt or decrypt a message.
The traditional type of cryptosystem used on a computer network is called a symmetric secret key system.
3) ANTIVIRUS
An antivirus program protects a computer against viruses by identifying and removing any computer viruses found in the computer memory, on storage media or incoming e-mail files. An antivirus program scans for programs that attempt to modify the boot program, the operating system and other programs that normally are read from but not modified.
IDENTIFYING VIRUS
Two technique are used to identify the virus.
If an antivirus program identifies an infected file, it attempts to remove its virus, worm or Trojan horse. If the antivirus program cannot remove the infection, it often quarantines the infected file. Quarantine is a separate area of a hard disk that holds the infected file until the infection can be removed. This step ensures other files will not become infected. Patents for inventions Utility, design or plant patents that protect inventions and improvements to existing inventions
4) ANTI-SPYWARE
Spyware is a program placed on a computer without the user’s knowledge. It secretly collects information about the user.
The spyware program communicates information to the outside source.
An anti-spyware application program sometime called tracking software or a spybot is used to remove spyware.
Among of the popular anti-spyware programs are:
• Spybot Search and Destroy
• Ad-aware
• Spyware Blaster
5) FIREWALL
Firewall is a piece of hardware or software which functions in a networked environment to prevent some communications forbidden by the security policy.
Firewall implement a security policy. It might permit limited access from in or outside the network perimeters or from certain user or for certain activities.
6) HUMAN ASPECTS OF SECURITY MEASURES
Human aspects refer to the user and also the intruder of a computer system.
It is one of the hardest aspects to give protection to.
The most common problem is the lack of achieving a good information security procedure
1) DATA BACKUP
Data Backup is a program of file duplication. Backups of data applications are necessary so that they can be recovered in case of an emergency.
2) CRYPTOGRAPHY
Cryptography is a process of hiding information by altering the actual information into different representation, for example, an APA can be written as I? X.
Almost all cryptosystems depend on a key such as a password like the numbers or a phrase that can be used to encrypt or decrypt a message.
The traditional type of cryptosystem used on a computer network is called a symmetric secret key system.
3) ANTIVIRUS
An antivirus program protects a computer against viruses by identifying and removing any computer viruses found in the computer memory, on storage media or incoming e-mail files. An antivirus program scans for programs that attempt to modify the boot program, the operating system and other programs that normally are read from but not modified.
IDENTIFYING VIRUS
Two technique are used to identify the virus.
If an antivirus program identifies an infected file, it attempts to remove its virus, worm or Trojan horse. If the antivirus program cannot remove the infection, it often quarantines the infected file. Quarantine is a separate area of a hard disk that holds the infected file until the infection can be removed. This step ensures other files will not become infected. Patents for inventions Utility, design or plant patents that protect inventions and improvements to existing inventions
4) ANTI-SPYWARE
Spyware is a program placed on a computer without the user’s knowledge. It secretly collects information about the user.
The spyware program communicates information to the outside source.
An anti-spyware application program sometime called tracking software or a spybot is used to remove spyware.
Among of the popular anti-spyware programs are:
• Spybot Search and Destroy
• Ad-aware
• Spyware Blaster
5) FIREWALL
Firewall is a piece of hardware or software which functions in a networked environment to prevent some communications forbidden by the security policy.
Firewall implement a security policy. It might permit limited access from in or outside the network perimeters or from certain user or for certain activities.
6) HUMAN ASPECTS OF SECURITY MEASURES
Human aspects refer to the user and also the intruder of a computer system.
It is one of the hardest aspects to give protection to.
The most common problem is the lack of achieving a good information security procedure
L17: INTRODUCTION COMPUTER THREATS
The computer is a great tool to store important information. In certain cases, the information is very vital that losing it will harm the computer system.
Computer threats can come from many ways either from human or natural disasters. For example, when someone is stealing your account information from a trusted bank, this threat is considered as a human threat. However, when your computer is soaked in heavy rain, then that is a natural disaster threat.
MALICIOUS CODE
Malicious code is also known as a rogue program. It is a threat to computing assets by causing undesired effects in the programmer’s part. The effect is caused by an agent, with the intention to cause damage.
The agent for malicious code is the writer of the code, or any person who causes its distribution. There are various kinds of malicious code. They include virus, Trojan horse, logic door, trapdoor and backdoor, worm and many others.
a) VIRUS
• a program that can pass on the malicious code to other programs by modifying them
• attaches itself to the program, usually files with .doc, .xls and .exe extensions
• destroys or co-exists with the program
• can overtake the entire computing system and spread to other systems
b) TROJAN HORSE
• a program which can perform useful and unexpected action
• must be installed by users or intruders before it can affect the system’s assets
• an example of a Trojan horse is the login script that requests for users’ login ID and password
• the information is then used for malicious purposes
c) LOGIC BOMB
• logic bomb is a malicious code that goes off when a specific condition occurs.
• an example of a logic bomb is the time bomb
• it goes off and causes threats at a specified time or date
e) TRAPDOOR OR BACKDOOR
• a feature in a program that allows someone to access the program with special privileges
f) WORM
• a program that copies and spreads itself through a network
Primary Differences Between Worms And viruses
Worm Virus
Operates through the network Spreads through any medium
Spreads copies of itself as a standalone program Spreads copies of itself as a program that attaches to other
programs
HACKER
Hacking is a source of threat to security in computer. It is defined as unauthorised access to the computer system by a hacker. Hackers are persons who learn about the computer system in detail. They write program referred to as hacks. Hackers may use a modem or cable to hack the targeted computers.
NATURAL AND ENVIRONMENTAL THREATS
Computers are also threatened by natural or environmental disaster. Be it at home, stores, offices and also automobiles.Examples of natural and environmental disasters:
Flood
Fire
Earthquakes, storms and tornados
Excessive Heat
Inadequate Power Supply
THEFT
Two types of computer theft:
1) Computer is used to steal money, goods, information and resources.
2) Stealing of computer, especially notebook and PDAs.
Three approaches to prevent theft:
1) prevent access by using locks, smart-card or password
2) prevent portability by restricting the hardware from being moved
3) detect and guard all exits and record any hardware transported
Computer threats can come from many ways either from human or natural disasters. For example, when someone is stealing your account information from a trusted bank, this threat is considered as a human threat. However, when your computer is soaked in heavy rain, then that is a natural disaster threat.
MALICIOUS CODE
Malicious code is also known as a rogue program. It is a threat to computing assets by causing undesired effects in the programmer’s part. The effect is caused by an agent, with the intention to cause damage.
The agent for malicious code is the writer of the code, or any person who causes its distribution. There are various kinds of malicious code. They include virus, Trojan horse, logic door, trapdoor and backdoor, worm and many others.
a) VIRUS
• a program that can pass on the malicious code to other programs by modifying them
• attaches itself to the program, usually files with .doc, .xls and .exe extensions
• destroys or co-exists with the program
• can overtake the entire computing system and spread to other systems
b) TROJAN HORSE
• a program which can perform useful and unexpected action
• must be installed by users or intruders before it can affect the system’s assets
• an example of a Trojan horse is the login script that requests for users’ login ID and password
• the information is then used for malicious purposes
c) LOGIC BOMB
• logic bomb is a malicious code that goes off when a specific condition occurs.
• an example of a logic bomb is the time bomb
• it goes off and causes threats at a specified time or date
e) TRAPDOOR OR BACKDOOR
• a feature in a program that allows someone to access the program with special privileges
f) WORM
• a program that copies and spreads itself through a network
Primary Differences Between Worms And viruses
Worm Virus
Operates through the network Spreads through any medium
Spreads copies of itself as a standalone program Spreads copies of itself as a program that attaches to other
programs
HACKER
Hacking is a source of threat to security in computer. It is defined as unauthorised access to the computer system by a hacker. Hackers are persons who learn about the computer system in detail. They write program referred to as hacks. Hackers may use a modem or cable to hack the targeted computers.
NATURAL AND ENVIRONMENTAL THREATS
Computers are also threatened by natural or environmental disaster. Be it at home, stores, offices and also automobiles.Examples of natural and environmental disasters:
Flood
Fire
Earthquakes, storms and tornados
Excessive Heat
Inadequate Power Supply
THEFT
Two types of computer theft:
1) Computer is used to steal money, goods, information and resources.
2) Stealing of computer, especially notebook and PDAs.
Three approaches to prevent theft:
1) prevent access by using locks, smart-card or password
2) prevent portability by restricting the hardware from being moved
3) detect and guard all exits and record any hardware transported
L16: COMPUTER SECURITY
DEFINITION OF COMPUTER SECURITY
Computer security means protecting our computer systems and the information they contain against unwanted access, damage, destruction or modification.
We need to protect our computer from any intruders such as hackers, crackers and script kiddie.
We do not want strangers to read our e-mail, use our computer to
attack other systems, send forged e-mail from our computer, or examine personal information stored on our computer such as financial statements.
TYPES OF COMPUTER SECURITY
Three types of computer security are:
a) hardware security
b) software security/data security
c) network security
a) HARDWARE SECURITY
Hardware security refers to security measures used to protect the hardware specifically the computer and its related documents.
The examples of security measures used to protect the hardware include PC-locks, keyboard-locks, smart cards and biometric devices.
b) SOFTWARE AND DATA SECURITY
Software and data security refers to the security measures used to protect the software and the loss of data files.
Examples of security measures used to protect the software are activation code and serial number.
c) NETWORK SECURITY
The transfer of data through network has become a common practice and the need to implement network security has become significant.
PERSONAL COMPUTER SECURITY CHECKLIST
In order to make sure our computers are secured, here are the computer
security checklist to follow.
Do not eat, drink or smoke near the computer
Do not place the computer near open windows or doors
Do not subject the computer to extreme temperatures
Clean the equipment regularly
Place a cable lock on the computer
Use a surge protector
Store disks properly in a locked container
Maintain backup copies of all files
Stores copies of critical files off sites
Scan a floppy disk before you open it
Do not open any unknown email received
Computer security means protecting our computer systems and the information they contain against unwanted access, damage, destruction or modification.
We need to protect our computer from any intruders such as hackers, crackers and script kiddie.
We do not want strangers to read our e-mail, use our computer to
attack other systems, send forged e-mail from our computer, or examine personal information stored on our computer such as financial statements.
TYPES OF COMPUTER SECURITY
Three types of computer security are:
a) hardware security
b) software security/data security
c) network security
a) HARDWARE SECURITY
Hardware security refers to security measures used to protect the hardware specifically the computer and its related documents.
The examples of security measures used to protect the hardware include PC-locks, keyboard-locks, smart cards and biometric devices.
b) SOFTWARE AND DATA SECURITY
Software and data security refers to the security measures used to protect the software and the loss of data files.
Examples of security measures used to protect the software are activation code and serial number.
c) NETWORK SECURITY
The transfer of data through network has become a common practice and the need to implement network security has become significant.
PERSONAL COMPUTER SECURITY CHECKLIST
In order to make sure our computers are secured, here are the computer
security checklist to follow.
Do not eat, drink or smoke near the computer
Do not place the computer near open windows or doors
Do not subject the computer to extreme temperatures
Clean the equipment regularly
Place a cable lock on the computer
Use a surge protector
Store disks properly in a locked container
Maintain backup copies of all files
Stores copies of critical files off sites
Scan a floppy disk before you open it
Do not open any unknown email received
L15: COMPUTER CRIMES
COMPUTER CRIMES
A computer crime is defined as any criminal activity that is related to the use of computers. These activities include computer fraud, copyright infringement, computer theft and computer attack.
COMPUTER FRAUD
Computer fraud is defined as having an intention to take advantage over or causing loss to other people, mainly on monetary basis through the use of computers.
COPYRIGHT INFRINGEMENT
Copyright infringement is defined as a violation of the rights secured by a copyright. Copyright infringement involves illegal copy or reproduction of copyrights material by the black market group. The open commercial sale of pirated item is also illegal.
COMPUTER THEFT
Computer theft is defined as the unauthorised use of another person’s property with the intention to deny the owner the rightful possession of that property or its use.
Examples of computer theft include:
• transfer of payments to the wrong accounts
• tap into data transmission lines on database at no cost
• divert goods to the wrong destination
COMPUTER ATTACK
Computer attack may be defined as any activities taken to disrupt the equipment of computer systems, change processing control or corrupt stored data.
Computer attack can be in the forms of:
• physical attack that disrupt the computer facility or its transmission lines.
• an electronic attack that uses the power of electromagnetic energy to overload computer circuitry.
• a computer network attack that uses a malicious code to exploit a weakness in software, or in the computer security practices of a computer user
A computer crime is defined as any criminal activity that is related to the use of computers. These activities include computer fraud, copyright infringement, computer theft and computer attack.
COMPUTER FRAUD
Computer fraud is defined as having an intention to take advantage over or causing loss to other people, mainly on monetary basis through the use of computers.
COPYRIGHT INFRINGEMENT
Copyright infringement is defined as a violation of the rights secured by a copyright. Copyright infringement involves illegal copy or reproduction of copyrights material by the black market group. The open commercial sale of pirated item is also illegal.
COMPUTER THEFT
Computer theft is defined as the unauthorised use of another person’s property with the intention to deny the owner the rightful possession of that property or its use.
Examples of computer theft include:
• transfer of payments to the wrong accounts
• tap into data transmission lines on database at no cost
• divert goods to the wrong destination
COMPUTER ATTACK
Computer attack may be defined as any activities taken to disrupt the equipment of computer systems, change processing control or corrupt stored data.
Computer attack can be in the forms of:
• physical attack that disrupt the computer facility or its transmission lines.
• an electronic attack that uses the power of electromagnetic energy to overload computer circuitry.
• a computer network attack that uses a malicious code to exploit a weakness in software, or in the computer security practices of a computer user
L14: CYBER LAW
What is Cyber Law?
Cyber law refers to any laws relating to protecting the Internet and other online communication technologies.
NEEDS FOR CYBER LAW
These concerns and issues clearly indicate why cyber laws are needed in online activities.
THE CYBER LAW ACTS IN MALAYSIA
The Malaysian Government has already passed several cyber laws to control and reduce the Internet abuse. These cyber laws include:
• Digital Signature Act 1997
• Computer Crimes Act 1997
• Telemedicine Act 1997
• Communications and Multimedia Act 1998
DIGITAL SIGNATURE ACT 1997
The Digital Signature Act 1997 secures electronic communications especially on the Internet. Digital Signature is an identity verification standard that uses encryption techniques to protect against e-mail forgery. The encrypted code consists of the user’s name and a hash of all the parts of the message.
COMPUTER CRIMES ACT 1997
The Computer Crimes Act 1997 gives protection against the misuses of computers and computer criminal activities such as unauthorised use of programmes, illegal transmission of data or messages over computers and hacking and cracking of computer systems and networks. By implementing the Computer Crimes Act 1997, users can protect their rights to privacy and build trust in the computer system. At the same time, the government can have control at a certain level over cyberspace to reduce cyber crime activities.
TELEMEDICINE ACT 1997
The Telemedicine Act 1997 ensures that only qualified medical practitioners can practice telemedicine and that their patient's rights and interests are protected.
These act provides the future development and delivery of healthcare in Malaysia.
COMMUNICATIONS AND MULTIMEDIA ACT 1998
The implementation of Communication and Telecommunication Act 1998 ensures that information is secure, the network is reliable and the service is affordable all over Malaysia.
This Act also ensures high level of user's confidence in the information and communication technology industry.
Cyber law refers to any laws relating to protecting the Internet and other online communication technologies.
NEEDS FOR CYBER LAW
These concerns and issues clearly indicate why cyber laws are needed in online activities.
THE CYBER LAW ACTS IN MALAYSIA
The Malaysian Government has already passed several cyber laws to control and reduce the Internet abuse. These cyber laws include:
• Digital Signature Act 1997
• Computer Crimes Act 1997
• Telemedicine Act 1997
• Communications and Multimedia Act 1998
DIGITAL SIGNATURE ACT 1997
The Digital Signature Act 1997 secures electronic communications especially on the Internet. Digital Signature is an identity verification standard that uses encryption techniques to protect against e-mail forgery. The encrypted code consists of the user’s name and a hash of all the parts of the message.
COMPUTER CRIMES ACT 1997
The Computer Crimes Act 1997 gives protection against the misuses of computers and computer criminal activities such as unauthorised use of programmes, illegal transmission of data or messages over computers and hacking and cracking of computer systems and networks. By implementing the Computer Crimes Act 1997, users can protect their rights to privacy and build trust in the computer system. At the same time, the government can have control at a certain level over cyberspace to reduce cyber crime activities.
TELEMEDICINE ACT 1997
The Telemedicine Act 1997 ensures that only qualified medical practitioners can practice telemedicine and that their patient's rights and interests are protected.
These act provides the future development and delivery of healthcare in Malaysia.
COMMUNICATIONS AND MULTIMEDIA ACT 1998
The implementation of Communication and Telecommunication Act 1998 ensures that information is secure, the network is reliable and the service is affordable all over Malaysia.
This Act also ensures high level of user's confidence in the information and communication technology industry.



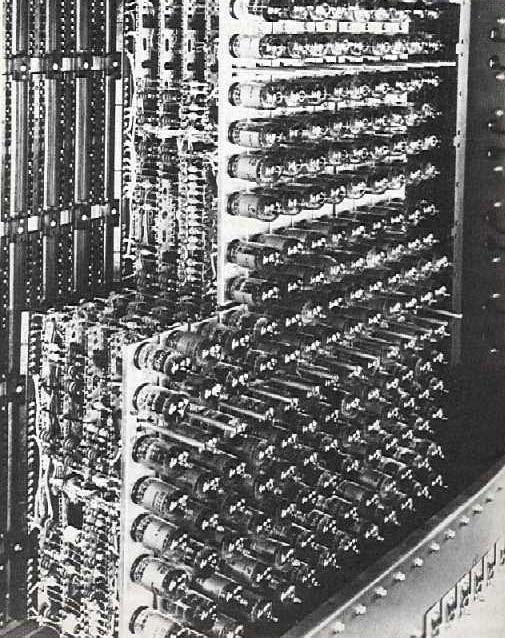 First Generation - 1940-1956: Vacuum Tubes
First Generation - 1940-1956: Vacuum Tubes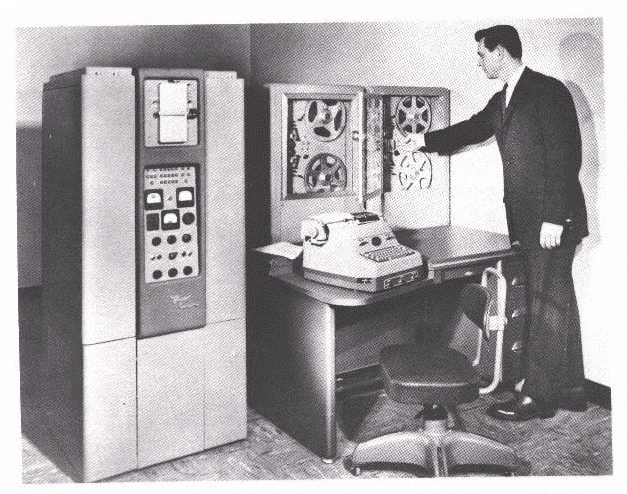 Second Generation - 1956-1963: Transistors
Second Generation - 1956-1963: Transistors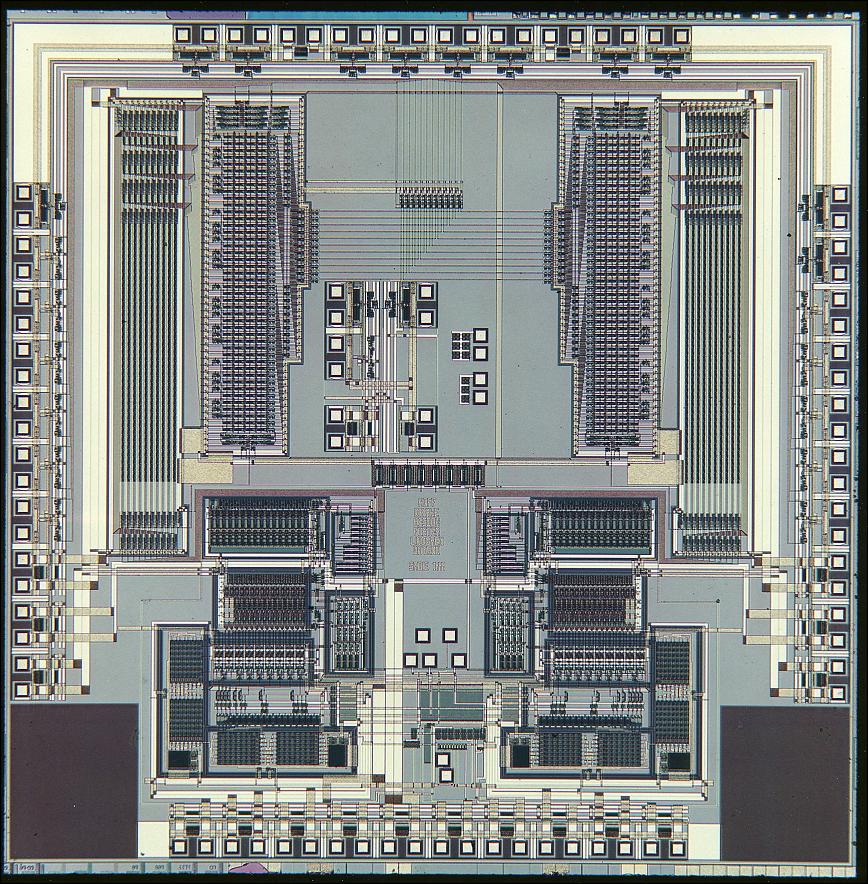 Third Generation - 1964-1971: Integrated Circuits
Third Generation - 1964-1971: Integrated Circuits
 Fifth Generation - Present and Beyond: Artificial Intelligence
Fifth Generation - Present and Beyond: Artificial Intelligence